Add extra security for your most sensitive data using encryption at rest for extracts
Update: The latest version of Tableau is here! Explore the newest innovations in this release.
Data encryption is a critical part of data security strategies to protect sensitive data. We understand you want to use Tableau for your most sensitive data and not miss out on the benefits offered when using extracts—like improved query performance. That’s why, starting with Tableau Server 2019.3, you can now encrypt your extracts at rest.
Think of this as object-level encryption. This means the data is translated at the object level (like a workbook or extract) into ciphertext, so that only authorized users can access the data in its original, readable state. In Tableau, it’s performant, secure, and easy to use—simply toggle it on per extract or enable encryption at the site level. Tableau Online is already fully encrypted at the service level.
Setting up encryption at rest to fit your needs
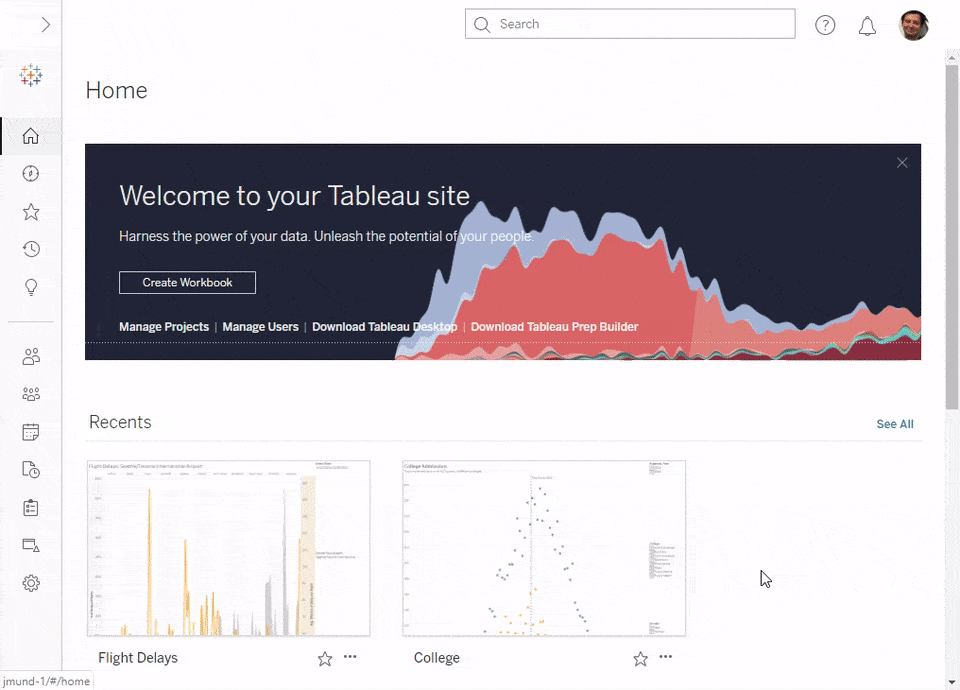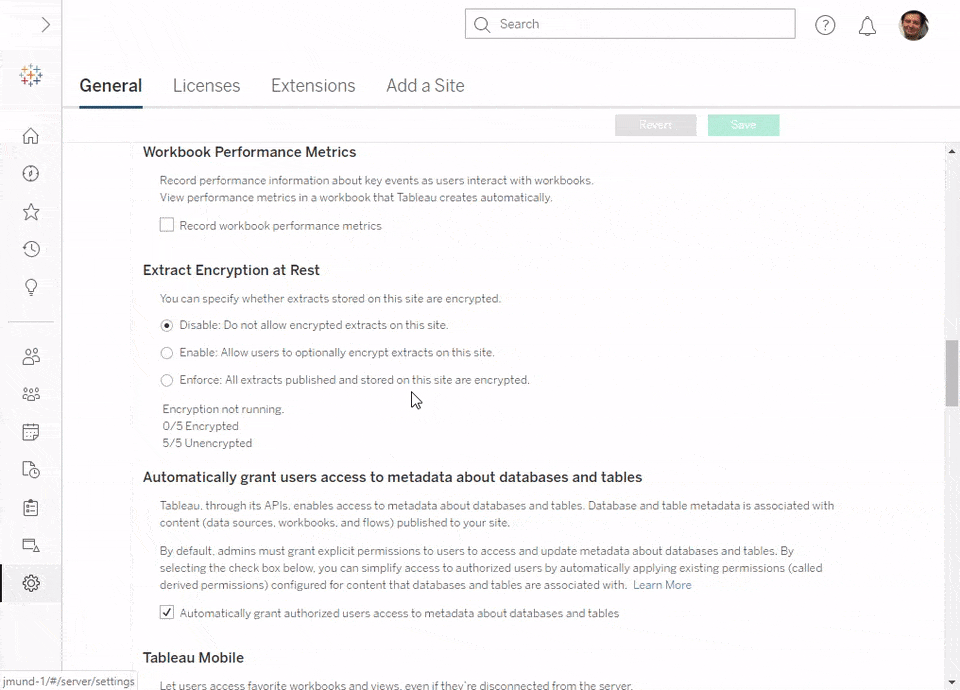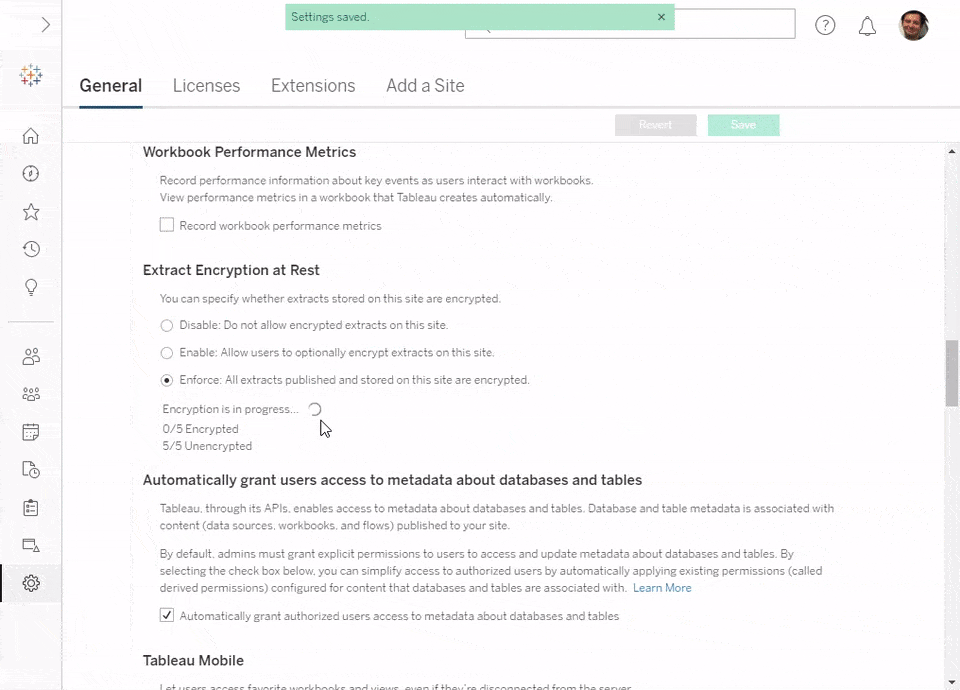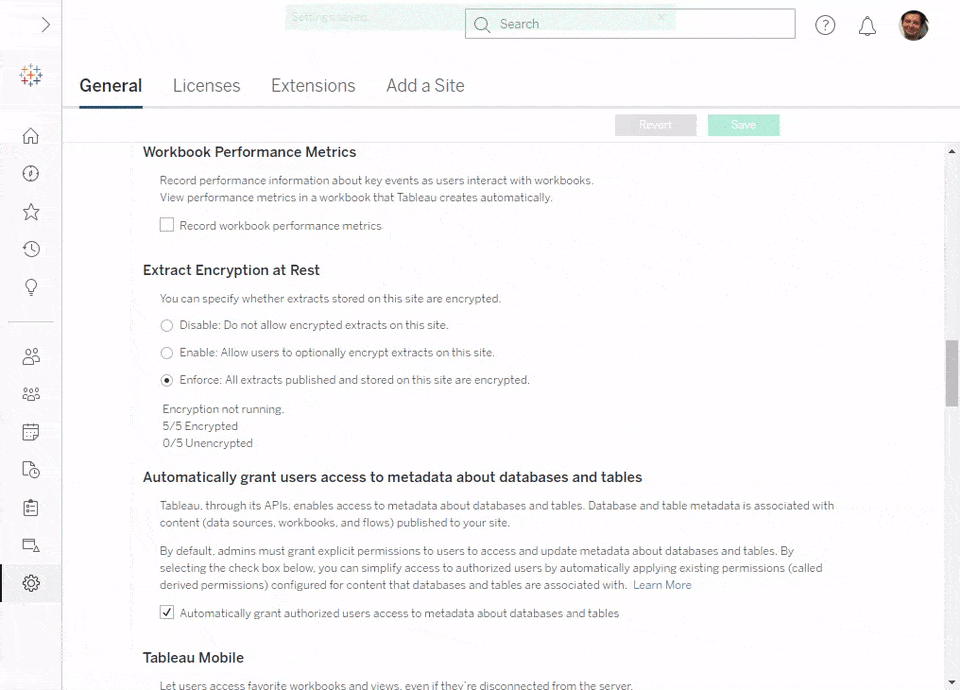
As a Tableau Server administrator, you have full control over how encryption can be used by configuring it at a per-site level. This allows you to align your encryption needs with how Tableau is used at your organization. For each site, you can choose between disabling, enabling, or enforcing encryption. To do this, go to Settings > General (or Settings > Manage all sites > Settings), and choose the encryption mode that fits best:
Enforced mode
If encryption is set to Enforced mode, all extracts published to the site are automatically encrypted by Tableau Server, whether published through Tableau Desktop, Tableau Prep Builder or Conductor, the REST API, or third-party tools like Alteryx or Informatica. Also, existing extracts on the site will be encrypted.
This includes Tableau extracts that are in the .tde file format—they will be automatically upgraded to encrypted .hyper files. If you don’t want this behavior, Enabled mode might be a better choice.
Enforced mode is recommended when (nearly) all extracts on a site contain sensitive content, and/or if your site admin wants the peace of mind that all data on the site will be secure. Keep in mind that enforcing encryption for everything can have tradeoffs—like potentially increased Backgrounder loads, increased viz load times, and impacts on backup and restore processes.
Enabled mode
In Enabled mode, encryption can be specified at the individual workbook, published data source, or prep flow level by the content owner. This mode supports the idea of self service in Tableau in that it empowers the content owners to decide to encrypt the data based on their knowledge of its sensitivity. In this mode, content owners can browse to their content and toggle encryption in the header:

Full and incremental refreshes on encrypted extracts will again result in encrypted extracts.
Enabled mode may be preferred when a site contains a mixture of both sensitive and non-sensitive data, and server resources are limited.
How encryption at rest works in Tableau Server
Behind the scenes, Tableau manages a key hierarchy to minimize the risk of disclosed information in case of compromised or outdated keys. Tableau Server’s master key can be managed by Tableau Server or Amazon Web Services Key Management Service (now in beta, management through AWS KMS is available with Tableau 2019.3 as part of the Tableau Server Management Add-on—formerly called Project McKinley).
Here is some additional, detailed information about how our encryption works:
- The encryption algorithm used is Advanced Encryption Standard (AES) with 256-bit keys, using the latest OpenSSL cryptomodule. More specifically, we use the Galois-Counter-Method (GCM) variant of the algorithm that also protects against unauthorized tampering with the data.
- Whenever toggling the encryption mode for existing content or for any newly published content, encryption jobs are scheduled on the server’s Backgrounder nodes. Please note that extract refresh jobs take precedence over encryption jobs to minimize impact on data freshness for your critical dashboards. Once encryption completes, the unencrypted extract will be deleted, and all new client sessions will use the encrypted extract.
- Encrypted extracts (embedded in workbooks or prep flows, or as part of published data sources) are decrypted during a download. If you want to prevent this, consider revoking download rights in Tableau Server.
- Extracts are stored in encrypted form in the backup image. Additionally, in order to maximize the availability of backups, all the information needed to restore a backup is included in the backup. When a site is exported, the extracts are decrypted and exported in cleartext. Backups and site export data must be handled securely for this reason. When the data is imported into the new site, it will be encrypted according to the site’s encryption policy.
Learn more and try encryption at rest in beta today
The Online Help page is a great starting point to dig deeper into encryption at rest. For additional security resources, including whitepapers, details on vulnerability reporting, and other documentation, visit www.tableau.com/security.
Check out the latest Tableau Server 2019.3 beta on our pre-release site and start exploring encryption at rest right now!
Verwante verhalen
Subscribe to our blog
Ontvang de nieuwste updates van Tableau in je inbox.








